نتایج جستجو

MALWARE DATA SCIENCE Attack Detection and Attribution
Joshua Saxe, 2018
Malware Data Science
Hillary Sanders & Joshua Saxe [Hillary Sanders], 2018
Malware Data Science: Attack Detection And Attribution
Joshua Saxe, Hillary Sanders, 2018
Malware Data Science: Attack Detection and Attribution
Joshua Saxe, Hillary Sanders, 2018
Malware Data Science: Attack Detection and Attribution
Joshua Saxe; Hillary Sanders, 2018
Malware Data Science: Attack Detection and Attribution
Joshua Saxe; Hillary Sanders, 2018
Beginning functional analysis
Karen Saxe, 2001
Collaborative Treatment of Traumatized Children and Teens: The Trauma Systems Therapy Approach
Glenn N. Saxe MD, B. Heidi Ellis PhD, Julie B. Kaplow PhD, 2006
Collaborative Treatment of Traumatized Children and Teens: The Trauma Systems Therapy Approach
Glenn N. Saxe, B. Heidi Ellis, Julie B. Kaplow, 2006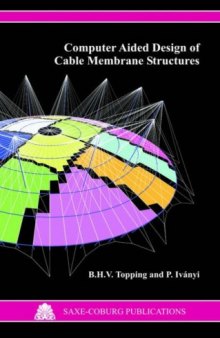
Computer Aided Design of Cable Membrane Structures (Saxe-Coburg Publications on Computational Engineering)
B. H. V. Topping, P. Ivanyi, 2008
Business Case for Network Security: Advocacy, Governance, and ROI
Catherine Paquet, Warren Saxe, 2004
The Business Case For Network Security Advocacy, Governance, And Roi - Cisco Press
Catherine Paquet, Warren Saxe, 2004
The Business Case for Network Security: Advocacy, Governance, and ROI
Catherine Paquet, Warren Saxe, 2004
Beginning functional analysis
Karen Saxe, 2002
Trauma Systems Therapy for Children and Teens, Second Edition
Glenn N. Saxe MD, 2015
Beginning functional analysis
Karen Saxe, 2002
Beginning Functional Analysis
Karen Saxe, 2001
Marshal Of France: The Life And Times Of Maurice, Comte De Saxe, 1696-1750
Jon Manchip White, 2011
Impacto social y ambiental del fracking
Benjamín Robles Montoya, John Saxe Fernández, 2014
Marshal Of France; The Life And Times Of Maurice, Comte De Saxe, 1699-1750
Jon Manchip White, 2016
The Prodigious Marshal: Being the Life and Extraordinary Adventures of Maurice De Saxe, Marshal of France
Edmund B. D'Auvergne, 2017![Marshal of France: The Life and Times of Maurice, Comte De Saxe [1696-1750]](http://cdn.ketabkoo.com/covers/17/1700141-n.jpg)




 مقالات ISI مرتبط
مقالات ISI مرتبط


